- Web Design Project
- 9 months ago
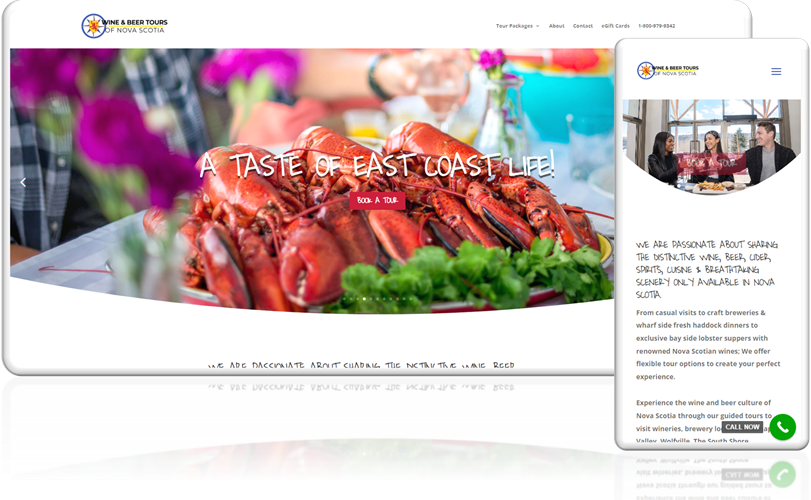
Wine & Beer Tour
Description: Wine & Beer Tour Wine and Beer Tours Nova Scotia Specializes in curated tours of th [...]
- Microhills
-
054469

Description: Wine & Beer Tour Wine and Beer Tours Nova Scotia Specializes in curated tours of th [...]
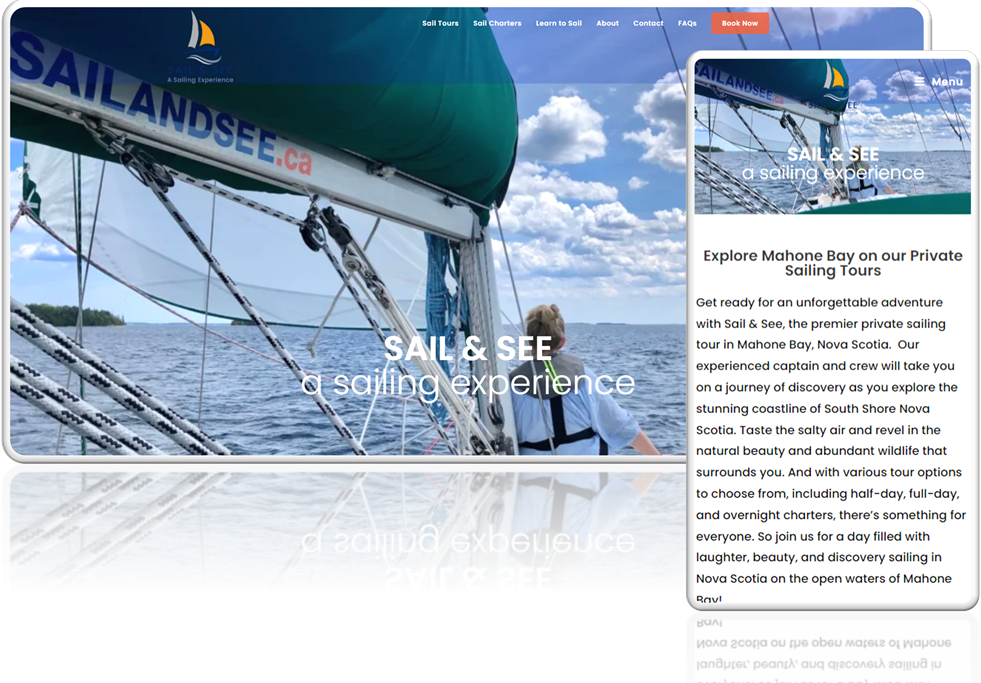
Description: Sail and See Sail and See offers unforgettable sailing experiences that allow guests to [...]
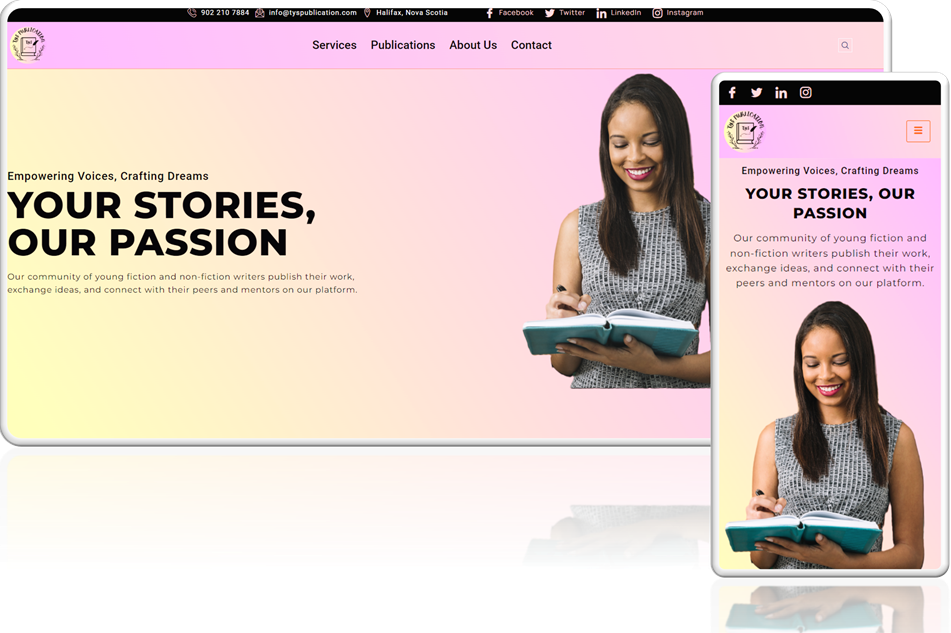
Description: TYS Publication TYS Publication provide a comprehensive and professional range of servi [...]
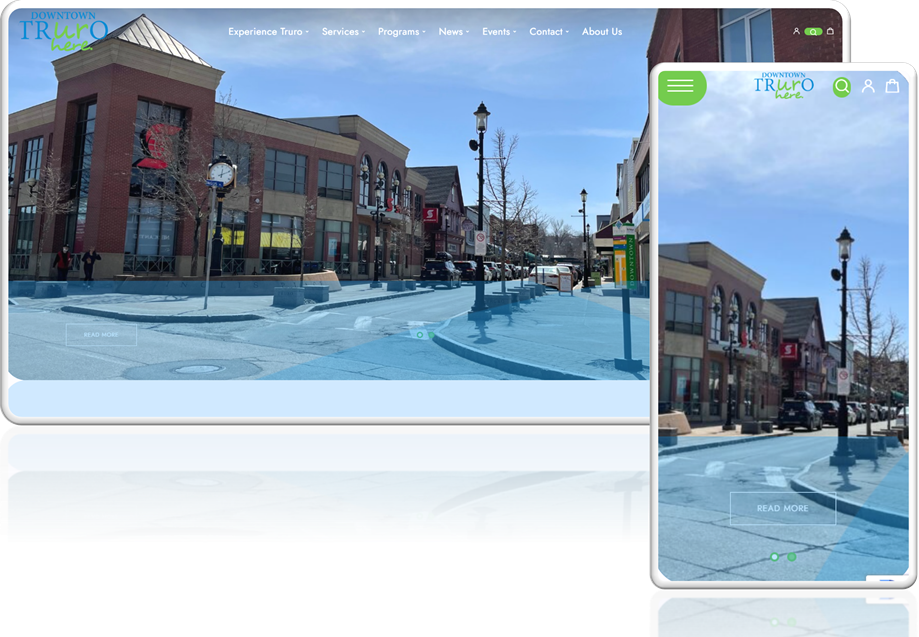
Description: Downtown Truro Downtown Truro supports local businesses and hosts various events throug [...]
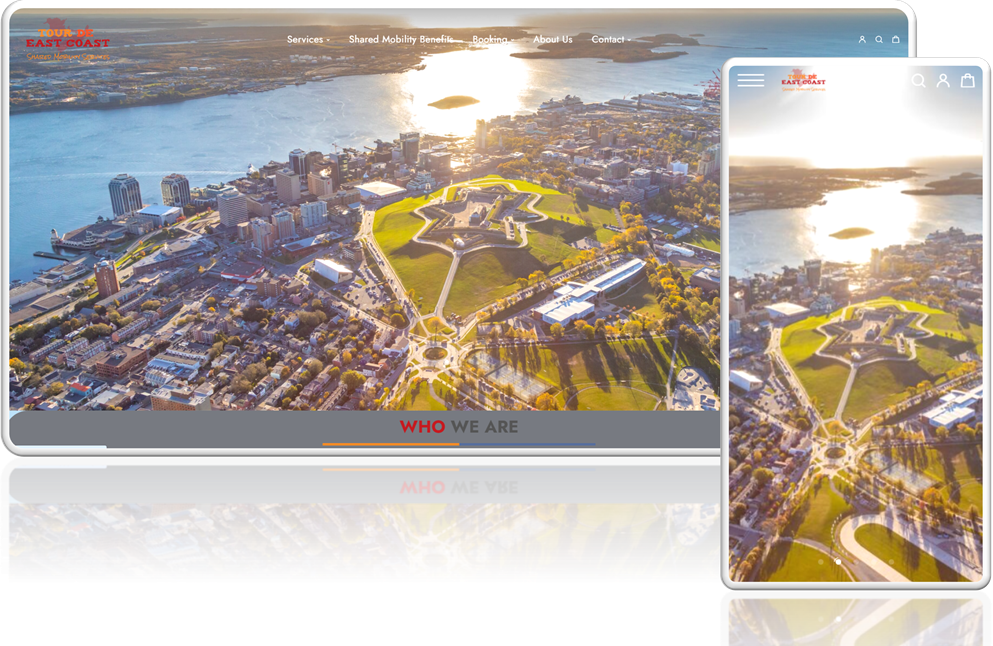
Description: Tour De East Coast Tour De Coast organizes memorable tours that highlight the unique at [...]
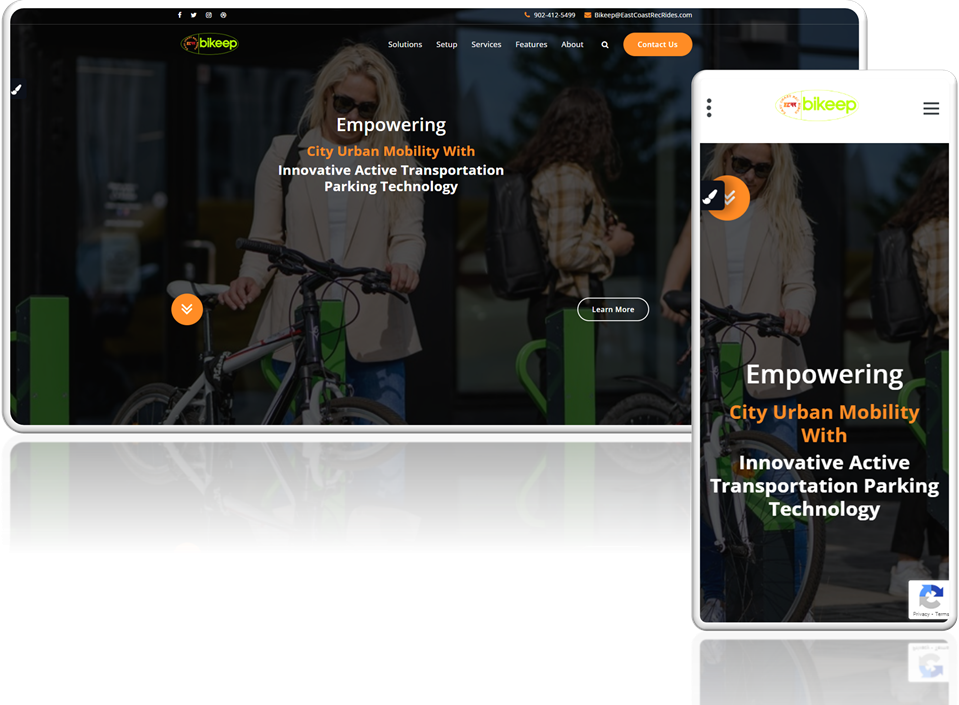
Description: East Coast Rec Rides Bikeep Bikeep provides innovative bike rental solutions that aim t [...]
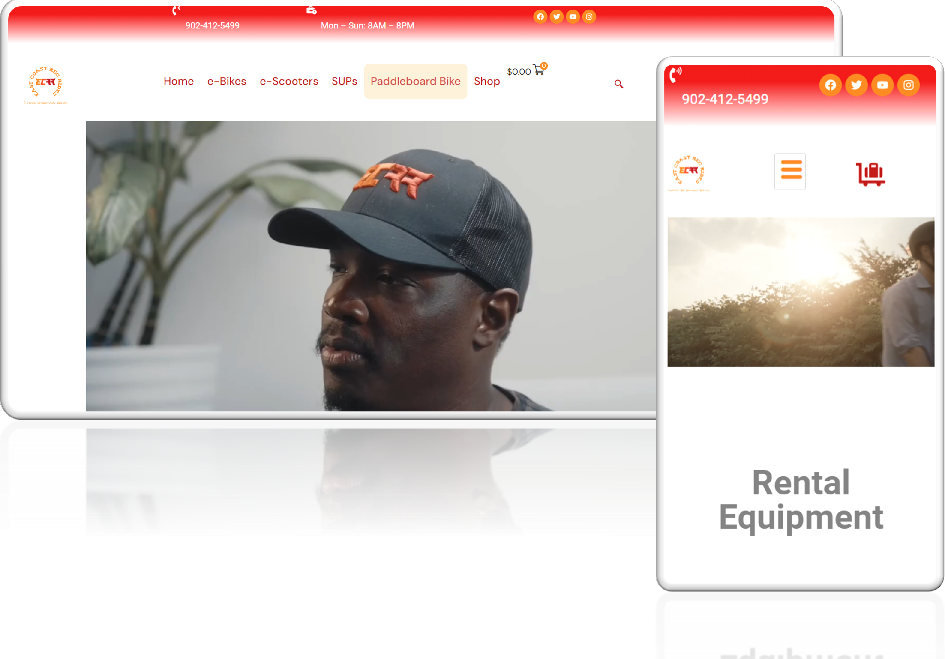
Description: East Coast Rec Rides Shop This retail shop specializes in high-quality biking gear and [...]
Company Overview: We are a leading information technology company, specializing in providing innovat [...]
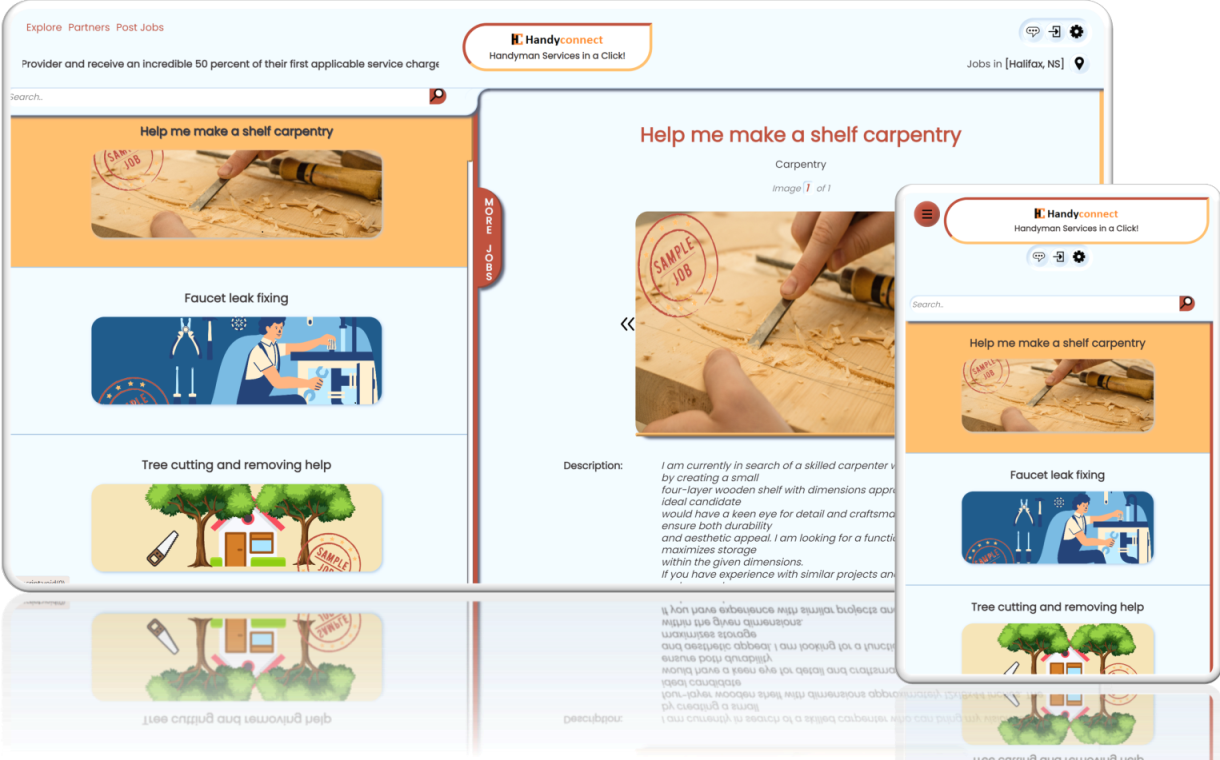
Description: The With Microhills Payment App provides hundreds of payment gateways for your customer [...]

Threat targets such as devices, information, and infrastructure can be vulnerable to threat actors w [...]